
File Server Resource Manager (FSRM) è un servizio ruolo in Windows Server che consente di gestire e classificare i dati memorizzati su file server. È possibile utilizzare Gestione risorse file server per classificare automaticamente i file, eseguire attività in base a queste classificazioni, impostare quote su cartelle e creare report per monitorare l’utilizzo dello spazio di archiviazione.
In questo tutorial vedremo come è possibile creare un filtro sul file per evitare di prendere dei ransomware.
Lanciare lo snap-in Gestione Risorse File Server
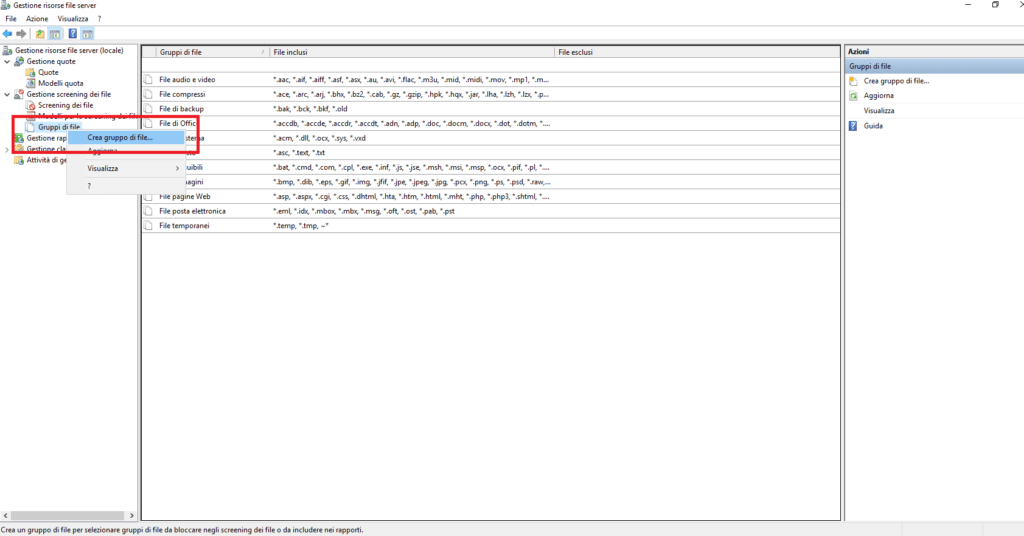
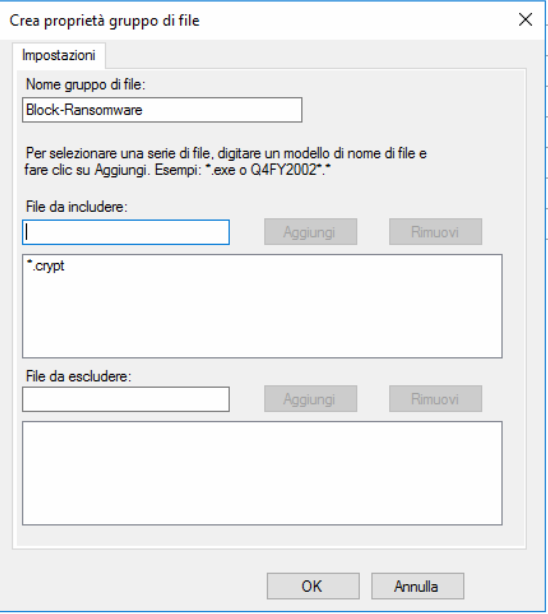
Cliccare su Gruppi di File quindi selezionare Crea Gruppo di File…
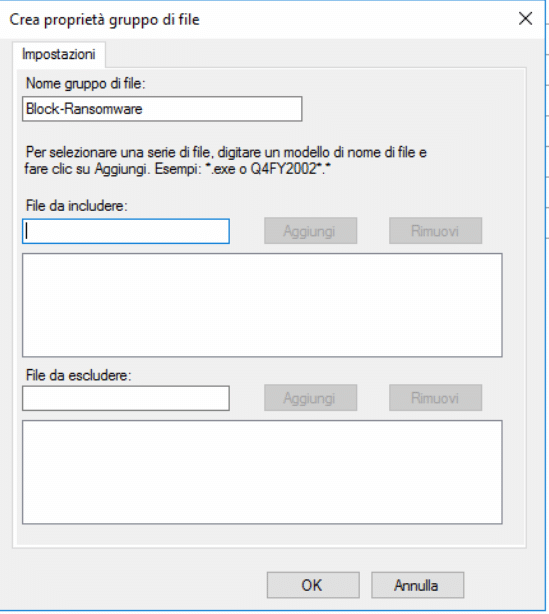
Inserire il nome del gruppo. Nel mio caso ho inserito Block-Ransomware
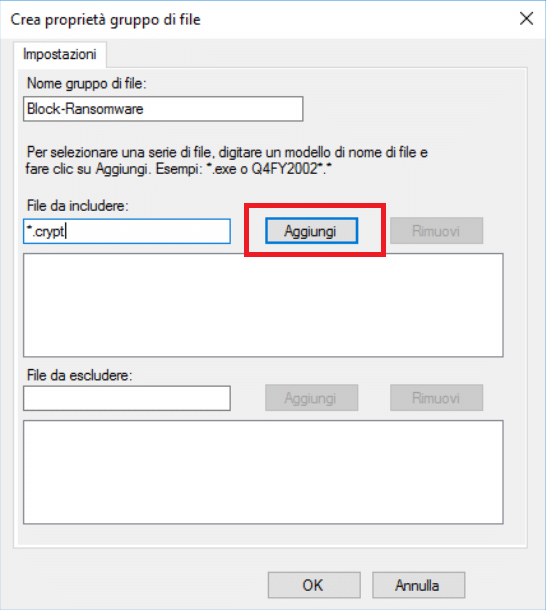
Inserire un estensione di un file da includere altrimenti non ci farà salvare il gruppo. (Ad esempio potete inserire *.crypt)
Quindi cliccare su Aggiungi
Cliccare OK per terminare la creazione del gruppo
Adesso da una Powershell eseguita con diritti amministrativi lanciare la seguente stringa di codice
NOTA BENE: cambiare solo il nome del gruppo (-Name “Block-Ransomware”) se l’avete creato con un nome diverso da Block-Ransomware quindi attendere qualche secondo fino al caricamento di tutte le estensioni.
|
0 |
Set-FsrmFileGroup -Name "Block-Ransomware" -IncludePattern @("*.muslat", "*.boston", "*.myskle", "*.pidom", "*.euclid", "*.heroset", "*.pidon", "*.kjh", "*.ERIS", "*.robbinhood", "*.[[email protected]].eth.hv88g2", "*.SONIC", "*.luboversova148", "*.lanset", "*.redmat", "*.dodger", "*.stone", "*.3674AD9F-5958-4F2A-5CB7-F0F56A8885EA", "*.harma", "*.[[email protected]].help", "*.rezuc", "*.2du1mj8", "*.FEROSUS", "*.hjgdl", "*.2k19sys", "*.mogera", "*.Hermes", "*.skymap", "*.[[email protected]].gate", "*.legacy", "*.datun", "*.rectot", "les#.TXT", "*.les#", "*.EZDZ", "*.open_readme.txt.ke3q", "*.ke3q", "*.ONYC", "*.NHCR", "*[email protected]", "*.[[email protected]].ETH", "*.[[email protected]].bat", "*.[SSSDKVNSDFITD]", "*.Pig4444", "*.bmn63", "*.[[email protected]].com", "*.[[email protected]].phoenix", "*[[email protected]].JSWORM", "*.[[email protected]].MERS", "*.n7ys81w", "*.jack", "*.ge010gic", "*.codnet1", ".codnat1", "*.codnet", ".codnat", "*.ferosas", "RESTORE_HCEEM_DATA.txt", "READ_ME.mars", "*.hceem", "*.vally", "*.mars", "Instructions with your files.txt", "*.refols", "*.carcn", "*.yum", "_CRYPTED_README.html", "*.ms13", "*.grovat", "[email protected]", "*.Mira", "*.Prodecryptor", "*[email protected]", "*.hrosas", "!QH24_INFO!.rtf", "*.QH24", "*.bkc", "*.mers", "*.wal", "*.recry1", "*.qbix", "*.aa1", "*.zoro", "Инструкция по расшифровке.TXT", "*.kes$", "*.condat", "*.dotmap", "*.4k", "*.ge0l0gic_readme.txt", "*.mamba", "*.ge0l0gic", "*.ddos", "Locked.*", ".PLUT", ".jack", "HowToBackFiles.txt", "DECRYPT-FILES.html", "*.non", "!!!INSTRUCTION_RNSMW!!!.txt", "*.drweb", "*.qbtex", "*.yG", "*.radman", "*.[[email protected]],", "!INSTRUCTI0NS!.TXT", "*.666decrypt666", "*[email protected]", "*.ztsysjz", "*[email protected]", "[email protected]", "*.[[email protected]].ws", "[[email protected]].Gate", "*.GGGHJMNGFD", "*.OOOKJYHCTVDF", ".eth", "*.PLUT", "*.bufas", "*.codnat1", "*.codnat", "*.fordan", "*.[[email protected]].bkc", ".nampohyu", "*.berost", "*.forasom", "*.{[email protected]}KBK", "*.fedasot", "*.[[email protected]].omerta", "*.sarut", "*.Navi", "*.dutan", "*.aes128ctr", "*.roldat", "*.hofos", "*.cheetah", "*.todarius", "*.FREDD", "*.Kiratos", "*.enc_robbinhood", "*.jzphmsfs", "*.[[email protected]].zoro", "*.verasto", "READ_ME.cube", "*.sambo,", "HELP_BY_CROC.TXT", "*.LDPR", "warning.txt", "*.guesswho", "*.moresa", "*.burn", "*.robinhood", "*.COLORIT", "*.SAVEYOURDATA", "*.aescrypt", "_HELP_INSTRUCTIONS_.TXT", "*[email protected]", "*.Ryuk", "*.croc", "*.norvas", "*.[[email protected]].phoenix", "*.CRABSLKT", "*.gotcha", "*.cube", "*.SDEN", "*.obagarmrk", "*.tater", "*.pumas", "*.browec", "*.hdeaf", "*.guvara", "*.tabufa", "*.tokog", "*.fuchsia", "*.etols", "*.[[email protected]]", "*.gate", "*.langolier", "*.spyhunter", "*.cryptoid", "*.[[email protected]].ETH", "*.Jumper", "*.major", "*.raldug", "*.phoenix", "*.gropas", "*.wannacash", "*.NGSC", "*[email protected]", "*._Crypted", "*.roland", "*.NOLOST", "*.Marozka", "*.encryptedALL", "*.stun", "*.grovas", "*.trosak", "*.tronas", "*.JLCW2", "*.[[email protected]].ETH", "*.drume", "*.securityP", "*.YYYYBJQOQDU", "ENCRYPTED.TXT", "*.MDEN", "README_LOCKED.txt", "README-NOW.txt", "*.locker", "*.proden", "*.CQQUH", "*[[email protected]].com", "*.luceq", "*.chech", "*.[[email protected]].GFS", "*.suffer", "*.инструкция по", "оплате.txt", "*.metan", "*.kezoz", "*.luces", "*.doples", "*.pdf_Axffyq_{[email protected]}.p3rf0rm4", "*.pdf.p3rf0rmr", "*.{[email protected]}CMG", "*.[[email protected]].amber", "*.L1LL", "*.charcl", "*.UIK1J", "*.kropun", "*.jimm", "*.klope", "*.[[email protected]].adobe", "*.jamper", "---README---.TXT", "*.[[email protected]].zq", "*.Scorpion", "*.pulsar1", "*.charck", "*.kroput1", "*.[[email protected]].ETH", "*.[[email protected]].ETH", "*.[[email protected]].ETH", "*.[[email protected]].ETH", "*.[[email protected]].ETH", "*.[[email protected]].ETH", "*[email protected]", "*.bRcrypT", "*.GILLETTE", "*.yatron", "*.kroput", "*.[[email protected]].plomb", "Restore_ICPICP_Files.txt", "HOW-TO-RESTORE-FILES.txt", "!#_How_to_decrypt_files_$!.txt", "_如何解密我的文件_.txt", "How to decrypt.txt", "*.[[email protected]", "*.Neptune", "*.{[email protected]}", "*.promorad2", "*.andymarvin", "*.mamasitaq", "*.cockista", "*.crabs", "*.dy8wud", "*.[[email protected]]", "*.kitty", "*.CIOP", "*.pfanz", "*.jcry", "*.evopro", "*.{[email protected]}MTP", "*.Annabelle2", "*.[[email protected]]", "*.promock", "*.promorad", "HOW TO DECRYPT[1T0tO].txt", "!_!email__ [email protected] __!..PAYMAN", "!SBLOCK_INFO!.rtf", "*.Frendi", "инструкция по", "оплате.txt", "how_to_recver_files.txt", "*.aqva", "!#_How_to_decrypt_files_#!", "SECURITY-ISSUE-INFO.txt", "! ПРОЧТИ МЕНЯ !.html", "*.cammora", "*.SBLOCK", "*.promoz", "*.crazy", "*.ARTEMY", "*.rontok", "*.crypt2019", "*.[[email protected]].aqva", "*.BlackPink", "*.id.*.crazy", "!GBLOCK_INFO.rtf", "*.GBLOCK", "*.cekisan", "*.promos", "*.seed", "*.jupstb", "*.KARLS", "!PEDANt_INFO!.rtf", "*.mecury", "*.PLANT", "#HELP-DECRYPT-FCRYPT1.1#.txt", "*.infileshop@gmail_com_ID44", "*.shadi", "*.dedo", "*[email protected]", "*.[[email protected]].ETH", "*.PEDANT", "*.Encrypted5", "*.Gefest3", "ClopReadMe.txt", "*.frend", "*.amber", "!!!READ_IT!!!.txt", "Readme_Restore_Files.txt", "Your files are now encrypted.txt", "HOW_TO_DECRYPT_MY_FILES.txt", "*.snake4444", "*.[[email protected]].888", "*.FCrypt", "*.Clop", "*.fastrecovery.xmpp.jp", "*.poyvonm", "*.crypted_pony_test_build_xxx_xxx_xxx_xxx_xxx", "*.FileSlack", "*.pluto", "*.paycoin", "*.blower", "*.nosafe", "*[email protected]", "*.secure", "*.crypted_pony_test_build*", "*.YOLO", "*.qwex", "*.DESYNC", "*.crash", "*.pennywise", "*.888", "*.*GEFEST", "*adobe.gefest", "*.OOFNIK", "*.[[email protected]].btc", "*.Mcafee", "*.mbrcodes", "*.UNIT09", "*.Xcri", "*.telebak", "*.[[email protected]]", "*.adobee", "*.mafee", "*.[[email protected]].btc", "*.GEFEST", "CRYPTOID_*", "*.PC-FunHACKED*", "TrumpHead.exe", "!README_GRHAN!.rtf", "*.ppam", "*.vaca", "*.heets", "*.alien", "*.SPCT", "anatova.txt", "anatova.exe", "170fb7438316.exe", "CallOfCthulhu.exe", "*.cripton", "*.GMBN", "*.ddpcbi", "*.[[email protected]]", "*.2lwnPp2B", "*[[email protected]].phobos", "*[email protected]_.btc", "*.RENSENWARE", "*.rumba", "*.AUF", "*.Tfudeq", "*.tfudet", "*.JAMES", "*.sdwwbrb", "*.ucftz*", "*.xcry7684", "*.eddldzor", "*.hncdumn", "*.g^od", "*.ezzyl", "*[email protected]*", "*.obfuscated", "*.rsucozxze", "*.mdk4y", "*.GRHAN", "*.zzzzzzzz", "*.bvjznsjlo", "*.sjjpu", "*.djuvq", "*.djvup", "*.djvut", "*.djvur", "*.djvus", "*.uudjvu", "*.udjvu", "*djvuu", "*.tfude", "*.tro", "*{[email protected]}.CORP", ".[[email protected]].*", "#RECOVERY_FILES#.txt", "*id-.LyaS", "$%%! NOTE ABOUT FILES -=!-.html", "*__{}.VACv2", "*.pdff", "*.djvuq", "*.INDRIK", "*[email protected]__*_.aes256.testE", "*[email protected]", "*.recovery_email_[[email protected]]*.aes256", "*.vulston", "*.SATANA", "*[[email protected]].rar", "*[email protected]", "*.ryx", "*.[[email protected]].костя", "*.nostro", "*.[[email protected]].combo", "*.mouse", "*.snatch", "*.bizer", "*.tunca", "*.[[email protected]].phobos", "*.locked_by_mR_Anonymous(TZ_HACKERS)", "*.ducueyuav", "*.oslawcmme", "*.Защищено", "*.Djvuu", "*.PRCP", "*.[[email protected]].adobe", "*.WORMCRYPT0R", "*.evolution", "*.cmsnwned", "*.ironhead", "*.ktuhzxpi", "*.elpvd", "*.kali", "*.Mercury", "*.[[email protected]].adobe", "*.FJ7QvaR9VUmi", "*.gerber5", "*.CRYPTR", "*.XY6LR", "cmdRansomware.*", "#RECOVERY_FILES#.*", "*.decryptgarranty", "_How to restore files.*", "_How_To_Decrypt_My_File_.*", "*.lucky", "*.PERSONAL_ID*", "*.garcewa", "*.danger", "*.israbye", "*.[[email protected]]", "*[email protected]", "*.iaufhhhhfiles_BACK_PLS_READ.html", "*.iaufhhhfiles_BACK_PLS_READ.html", "*.hilegofprencrp", "*.wowreadfordecry", "*.btc -help-you", "*.checkdiskenced", "*.iloveworld", "*.goforhelp", "*.encmywork", "*.[[email protected]].adobe", "*.[[email protected]].adobe", "*.crypted_bizarrio@pay4me_in", "*.DeLpHiMoRiX*", "*.malwarehunterteam", "*.demonslay335_you_cannot_decrypt_me!", "*.peosajwqfk", "*[email protected]", "*.risk", "*.[[email protected]].war", "*[email protected]", "*.myjob", "*.lolita", "*snowpicnic*", "*SIMMYWARE*", "how to get back you files.txt", "*.cccmn", "aboutYourFiles.*", "*wall.i", "#RECOVERY-PC#.*", "!-GET_MY_FILES-!.*", "@_RESTORE-FILES_@.*", "*.Puma", "*.[[email protected]][email protected]", "*.kraussmfz", "*.PUMAX", "*.anami", "*.449o43", "*.DeLpHiMoRiX!@@@@_@@_@_2018_@@@_@_@_@@@", "*.[[email protected]].adobe", "*.Enter", "*.betta", "*.INFOWAIT", "*.FIXT", "*.fire", "*.Horsuke", "*.Vapor", "*.ispfv", "*.Bear", "*.EnyBenied", "*.BlackHat", "*.Epoblockl", "*.DATAWAIT", "*.010001", "*.AUDIT", "*.[papillon9275]", "*.UKCZA", "*.YIAQDG", "*.CQXGPMKNR", "*.HHFEHIOL", "*.GrujaRS", "*.xuy", "*.crypted034", "*.FilGZmsp", "*.krzffw", "*.impect", "*.fast", "*.Ox4444", "*.6db8", "*.PTGEPVEKM", "*.adobe", "*.JKOUOGVG", "*.mariacbc", "*[email protected]", "*.SYMMYWARE", "*.vendetta2", "*.xxxxx", "*.CommonRansom", "*.crypt888", "*.gdb", "*[email protected]", "*.WAND", "*.[[email protected]].EVEREST", "*.FUNNY", "*.vanss", "*.SANTANA", "*.NOT", "*.beer", "*.SOLO", "*.GMPF", "*.W0YR8", "*.charm", "*.birbb", "TOTALLYLEGIT.EXE", "*[email protected]", "*[email protected]", "*.THDA", "*.katyusha", "*.LGAWPULM", "*.[[email protected]].gamma", "*.101", "*.zlpzdel", "*.junked", "*.DQXOO", "*.NOBAD", "*.garrantydecrypt", "*.BAWSUOOXE", "*.Kg9EX", "*.EMAN50", "*.[[email protected]].crab", "!!!ReadMeToDecrypt.txt", "*.qweuirtksd", "#README_GMAN#.rtf", "!README_GMAN!.rtf", "*.GMAN", "*.boost", "*.ziqzqzdi", "52036F92.tmp", "*.FFF", "*.911", "*.2xx9", "*.@decrypt_2017", "(encrypted)*", "*zn2016", "#HOW_DECRYPT_FILES#.html", "!back_files!.html", "*.Bill_Clinton@derpymailorg", "*.nWcrypt", "*.needkeys", "*.YAYA", "*.write_on_email", "*.needdecrypt", "*.0402", "*.NIGGA", "HOW_DECRYPT_FILES#.html", "*.eQTz", "*.aRpt", "*.3P7m", "*.3RNu", "*.rpd", "*.[[email protected]].dharma", "HOW TO RECOVER ENCRYPTED [email protected]", "READ_TO_DECRYPT.html", "*.[[email protected]].embrace", "*[[email protected]].bip", "*[[email protected]].write", "#NEWRAR_README#.rtf", "Files encrypted.html", "*.backup", "*[java2018@tuta io].arrow", "!OoopsYourFilesLocked!.rtf", "*[[email protected]]", "*.[[email protected]].btc", "How To Restore Files.txt", "*.bgtx", "Info.hta", "FILES ENCRYPTED.txt", "*.DHDR4", "*.crypted_marztoneb@tutanota_de", "YOU_MUST_READ_ME.rtf", "*How to Decrypt Files-*.html", "*.BaLoZiN", "*.RJZUNA", "*@LOCKED", "*.EMAN", "*.firmabilgileri", "*-DECRYPT.txt", "*.iudgkwv", "*.[[email protected]].NOT_OPEN", "ReadMe_Decryptor.txt", "!_HOW_RECOVERY_FILES_!.txt", "READ__IT.txt", "*.f*cked", "*-DECRYPT.html", "*.[[email protected]].brrr", "*.spaß", "*.olduw", "*.yoewy", "*.BDKR", "*.onlinesupport", "*.anonymous", "*.bkp", "*.ryk", "*.skype", "*.CHE808", "*.parrot", "*.monro", "*.NOT_OPEN", "*.no_more_ransomware", "*.gamma", "*.brrr", "*.Nano", "*.ITLOCK", "*.SAVEfiles", "*.mvp", "*.hitler", "*.mammon", "*.SLAV", "*[email protected]", "*[[email protected]].pip", "*.KOK08", "*.eoeo", "*.FASTBOB", "*.lockymap", "*.NEWRAR", "*.cryptoNar", "*.partially.cryptoNar", "*.PICO", "*.CYBERGOD", "*.rcrypted", "*.kvllyatprotonmaildotch", "*.KOK8", "*.fsdfsdfsdfsdfsdfsfdsfs", "How To Decode Files.hta", "*.BadNews", "*.cassetto", "*.sophos", "*.{[email protected]}.ARA", "*.[[email protected]].CreamPie", "*.FuckedByGhost", "*.#__EnCrYpTED_BY_dzikusssT3AM_ransomware!__#", "*.lockedfile", "*.WHY", "*.AlfaBlock", "# How to Decrypt Files.txt", "*-Lock.onion", "*.PrOtOnIs.VaNdElIs", "*.PrOtOnIs", "*.Armage", "*.rent", "*.fox", "*.pleaseCallQQ", "*.lockedgood", "*.hacked.by.Snaiparul", "*.ShutUpAndDance", "*.K8VfiZ", "*.G8xB", "*.cmb", "*.b29", "*.poolezoor", "*.id-*.cmb", "*.KEYPASS", "*.doubleoffset", "*.tedcrypt", "!=How_to_decrypt_files=!.txt", "*.divine", "*.wannacryv2", "*[email protected]", "*.dragnea", "*.RECOVERYOURFILES", "*.invaded", "*.incpas", "*.BARRACUDA", "*.sdk", "*.cryptes", "*.like", "*.ukrain", "*.dfjhsalfhsakljfhsljkahfdjklashfdjklh", "*.black007", "*.combo", "*[email protected]", "*0nl1ne*", "*.locked.zip", "*.boris", "*.powerfuldecrypt", "*.predator", "*.XERO", "*.HYENA", "*.BD.Recovery", "*.zzz12", "*king_ouroboros*", "*.dyaaghemy", "*.[[email protected]]", "*.DATASTOP", "*.thunder", "*.LanRan*", "*.deep", "*.TaRoNiS", "*.desu", "*.SHRUG2", "*.[[email protected]].thunder", "*.LanRan2.0.5", "*.[[email protected]]", "*.jewsomware", "*.[[email protected]].lock", "*.##___POLICJA!!!___TEN_PLIK_ZOSTA", "*.animus", "*.[[email protected]].EVIL", "*.[[email protected]].bin", "*.DATA_IS_SAFE_YOU_NEED_TO_MAKE_THE_PAYMENT_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_LOST_FOREVER_PLEASE_BE_REZONABLE_IS_NOT_A_JOKE_TIME_IS_LIMITED", "*.XVNAW", "*.24H", "*.[[email protected]].eV3rbe", "*.SHRUG", "*.KUAJW", "*.[[email protected]].meduza", "*[email protected]", "*[[email protected]].HRM", "*[[email protected]].HRM", "*.choda", "*.ransomcrypt", "FILES.TXT", "*.nozelesn", "*.KRAB", "*.Aurora", "*.bomber", "*.BtcKING", "*.CyberSCCP", "*[email protected]", "*.PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_to_make_the_payment", "*@cock.email", "*.recme", "*.king_ouroboros*", "*.omerta", "*.[[email protected]].omerta", "*.donut", "*.volcano", "*.jungle@anonymousspechcom", "*.Alkohol", "*.oneway", "*.ONYX", "*[email protected]", "*.BIG4+", "*.leen", "*[email protected]", "*.DiskDoctor", "*.qnbqw", "*[email protected]", "*[email protected]", "*[email protected]", "*[email protected]", "*.billingsupp", "*.ndpyhss", "*.SF", "*[email protected]", "RESTORE-SIGRUN.*", "*id-*.BI_ID", "*.cryptgh0st", "*.emilysupp", "*.RedEye", "*.AdolfHitler", "*.crybrazil", "*[email protected]", "*.REBUS", "filesinfo.txt", "!!!!RESTORE_FILES!!!.txt", "*.insta", "*.CONTACTUS", "*.osk", "*.[[email protected]].pain", "*.embrace", "Decoding help.hta", "*.karne", "*[email protected]", "*.decodeme666tutanota_com", "*.josep", "*.decodeme666@tutanota_com", "*.cdrpt", "*.SEPSIS", "*[email protected]", "*.sigrun", "*.booknish", "*.bip", "*.[[email protected]].SEPSIS", "*.MTXLOCK", "*.RansomAES", "*.PAUSA", "*.hac", "*.[[email protected]].china", "*.UselessFiles", "*.GrAnoSinSa", "*.rand", "HOW DECRIPT FILES.hta", "*.kcwenc", "*.mich", "*.OBLIVION", "*.cryptfile", "*.BlackRouter", "*.pay2me", "*.Satyr", "*.sorry", "*.tron", "*.sky", "*.NMCRYPT", "*@tutanota.com]", "*@tuta.io]", "*.Horros", "*.LolSec", "Perfect.sys", "*.d3g1d5", "*.excuses", "*.cock.email", "*.MOLE66", "*.*.sell", "UselessDisk.exe", "*.EGG", "*.JFCWF", "wormDll*.dll", "ScreenLocker_x86.dll", "SsExecutor_x86.exe", "Spreader_x86.dll", "tabDll*.dll", "Zenis-*.*", "*.xwz", "*.Stinger", "0000-SORRY-FOR-FILES.html", "READ_ME_HELP.png", "READ_ME_HELP.txt", "*.[[email protected]].java", "*.FRS", "Zenis-Instructions.html", "*.[[email protected]].arena", "*.koreaGame", "*.improved", "*.[[email protected]].volcano", "*@adsoleware.com*", "*.kwaaklocked", "_XiaoBa_Info_.hta", "*.XiaoBa", "*.cypher", "*.bananaCrypt", "*BlockBax*", "ownertrust.txt", "qwerty-pub.key", "*.igza4c", "*.Nutella", "*.[[email protected]].everbe", "*.Sil3nt5pring", "*.Crab", "*.jodis", "*.jes", "*.Bitconnect", "*.arrow", "*[email protected]", "*.leenapidx", "*.creeper", "*.Encrypted[[email protected]].XiaBa", "*.styver", "*[email protected]", "*.YOU-ARE-FUCKED-BY-BALILUWARE-(CODED-BY-HEROPOINT)", "*.frmvrlr2017", "*.SUSPENDED", "Restore Files.TxT", "*.ANNABELLE", "*.messenger-*", "*.[ID62133703]", "*.nazcrypt", "*.THANATOS", "*.ransomwared", "*.saturn", "*.干物妹!", "*.happyness", "*[[email protected]].java", "*[email protected]*", "*.Tornado", "*.david", "*.defender", "*.blank", "matrix-readme.rtf", "WhatHappenedWithFiles.rtf", "WhatHappenedWithMyFiles.rtf", "Readme-Matrix.rtf", "#_#WhatWrongWithMyFiles#_#.rtf", "*_[[email protected]][JINNYG@TUTANOTA", "*.honor", "*.twist", "*ReadMe_Decryptor.txt", ".[[email protected]].dcrtr", "*.blackruby", "*.justice", "*.adam", "*...Files-Frozen-NEED-TO-MAKE-PAYMENT…", "*.[[email protected]].java", "*.bunny", "*.lockme", "*.DREAM", "*.same", "*.write", "*.b89b", "*.GDCB", "*.[[email protected]].java", "*.block", "*.DEUSCRYPT", "*.notfoundrans", "*.howcanihelpusir", "*.happenencedfiles", "*.AreYouLoveMyRansFile", "*.country82000", "*.insane", "*.qwerty", "*.LOCKED_BY_pablukl0cker", "*.[[email protected]].insane", "*.velso", "*.[[email protected]].java", "*.[[email protected]].java", "*.PLANETARY", "*.CryptWalker", "*.Infinite", "*.[[email protected]].java", "*.LTML", "*.[[email protected]].java", "*.kryptonite", "*.Server", "*.leon", "*.vrmrkz", "*.1btc", "*.[[email protected]].java", "*.id-02B52D6C.[[email protected]].java", "*.sysdown", "*.gigahertz", "*.rapid", "*.triple_m", "*.info", "*.weapologize", "*.tastylock", "*.blind2", "*.STOP", "*.wtf", "*.[[email protected]].napoleon", "*.File", "*.[[email protected]].java", "*.godra", "*.maniac", "*.VENDETTA", "*.[[email protected]].java", "*.[[email protected]].java", "*.satan", "*.fix", "*.GORILLA", "*.CHRISTMAS", "*.[[email protected]]*.wallet", "*.492", "*.Cyclone", "*.katipuneros", "*.styx", "*.RDWF", "*.wmfxdqz", "*.Work", "*.noblis", "*.DS335", "*.[[email protected]].skeleton", "*.e4m", "*.encencenc", "*.executioner", "*.CerBerSysLocked0009881", "*.spider", "*.[[email protected]].blind", "*.0wn3dyou", "*.Frivolity", "*.lime", "*.[[email protected]].arena", "_READ_ME_FOR_DECRYPT.txt", "*.[[email protected]].wallet", "*.eTeRnItY", "*.bit", "*.dxjay", "*.dwbiwty", "*.xhspythxn", "*.fbuvkngy", "*.RansomMine", "*.MTC", "*.napoleon", "*.dlenggrl", "*.TEST", "*.GOTYA", "*.maxicrypt", "*.[[email protected]].maxicrypt", "*.encrptd", "*.vpgvlkb", "*.areyoulovemyrans", "*.shadow", "*.[[email protected]].scarab", "*.cock.li", "*.aajf", "*.iGotYou", "*.Ipcrestore", "*.PHOBOS", "*.fairytail", "*.fucku", "*.basslock", "*.wdie", "*.wsmile", "*.wndie", "*.0000", "*.RASTAKHIZ", "*.PANDA", "*.BIG1", "*.TRUE", "*.am", "*.kill", "*.kimchenyn", "*.XZZX", "*.fat32", "*.##ENCRYPTED_BY_pablukl0cker##", "*aes_ni_gov", "*.aes_ni", "*.bloked", "*.cripted", "*.filesfucked", "*.cryptx*", "*.how_to_recover*.*", "*.help_restore*.*", "*.restore_fi*.*", "*.ukr.net*", "*.qq_com*", "Wo_sind_meine_Dateien.htm*", "*.fake", "*.cobra", "*].block", "!!!GetBackData!!!.txt", "*.HRM", "*.skvtb", "*.game", "*.Losers", "*.gr3g", "*.oni", "*.sinta", "*[email protected]", "*.xiaoba33", "*.xiaoba32", "*.xiaoba31", "*.xiaoba30", "*.xiaoba29", "*.xiaoba28", "*.xiaoba27", "*.xiaoba26", "*.xiaoba25", "*.xiaoba24", "*.xiaoba23", "*.xiaoba22", "*.xiaoba21", "*.xiaoba20", "*.xiaoba19", "*.xiaoba18", "*.xiaoba17", "*.xiaoba16", "*.xiaoba15", "*.xiaoba14", "*.xiaoba13", "*.xiaoba12", "*.xiaoba11", "*.xiaoba10", "*.xiaoba9", "*.xiaoba8", "*.xiaoba7", "*.xiaoba6", "*.xiaoba5", "*.xiaoba4", "*.xiaoba3", "*.xiaoba2", "*.XiaoBa1", "*.XiaoBa34", "*[email protected]", "allcry_upx.exe", "*-PLIIKI.txt", "dispci.exe", "cscc.dat", "infpub.dat", "LEIA_ME.txt", "*.lordofshadow", "*.SaherBlueEagleRansomware", "*.[[email protected]].CRIPTOGRAFADO", "[email protected]________.rar", "How_Decrypt_Files.hta", "*.Ordinal", "*.aes!", "READ_ME_FOR_DECRYPT_*.txt", "*.ihsdj", "*.kgpvwnr", "*.LIN", "*.CHAK", "*.Chartogy", "*.viiper", "*.x1881", "*.stroman", "*.asasin", "*.BUGWARE", "*.SENRUS17", "!! RETURN FILES !!.txt", "*.loveransisgood", "*.PayDay", "*.allcry", "*.lockd", "*.PRIVAT66", "*.SHARK", "005-DO-YOU-WANT-FILES.html", "*.#", "*.CyberSoldiersST", "*.wyvern", "*.technicy", "*.cyberdrill", "*.ZW", "*.myransext2017", "*.ykcol", "*.XmdXtazX.", "*[email protected]", "*.cryptojoker", "*.Doxes", "*.XmdXtazX", "*.blind", "*.Locked_file", "*.HeroesOftheStorm", "*.dian", "*.mind", "*.H_F_D_locked", "*.reaGAN", "*.INCANTO", "*.pablukCRYPT", "*.gocr", "*.revolution", "*.disposed2017", "*.armadilo1", "*[email protected]", "*.[[email protected]].arena", "_RECoVERY_+*.*", "*.__dilmaV1", "*.hacked", "*.[[email protected]].nuclear", "READ_THIS_FILE_1.TXT", "*.pnr", "*.{[email protected]}.BRT92", "*.ILLNEST", "*.OhNo!", "*.akira", "*..txt", "*.3nCRY", "*.clinTON", "RESTORE_INFO-*.txt", "*.BUSH", "*.[[email protected]].nuclear", "*.CryptedOpps", "*.crypt12", "*.OTR", "Important_Read_Me.txt", "*.JezRoz", "*.UNLIS", "*.granny", "*.shinigami", "*.PA-SIEM", "*.flat", "TUTORIEL.bmp", "*.xolzsec", "*.Flux", "*.Blocked2", "*.wooly", "*.nuclear", "*.area", "*.EMPTY", "*.arena", "lukitus.html", "*.zuzya", "*.{[email protected]}.BRT92", "*.CYRON", "*.#Locky", "*.ERROR", "*.EV", "*.lokitus", "*.lukitus-tiedostopäätettä", "*.fmoon", "*.cesar", "*.lukitus", "*.KK", "*.prosperous666", "*.[[email protected]].onion", "*.encrypted[[email protected]]", "*.enc", "*.anubi", "*.D2550A49BF52DFC23F2C013C5", "*.LEGO", "*[email protected]", "*.0x009d8a", "*.3301", "*.ZABLOKOWANE", "*.pabluklocker", "*.cezar", "*.cnc", "*.trump", "*.Crypton", "*.rumblegoodboy", "*.BONUM", "*.[[email protected]]", "diablo6-*.htm", "*.DIABLO6", "*.PEDO", "*.HELLO", "*.ACTUM", "*.OGONIA", "*.WAmarlocked", "!## DECRYPT FILES ##!.txt", "*.nopasaran", "*.gryphon", "ebay-msg.html", "ebay_was_here", "*.ebay", "*.491", "*.mtk118", "*.490", "*.shutdown57", "*.PIRATE", "*.wxdrJbgSDa", "*.sea", "*.PLIN", "*.726", "*.SEVENDAYS", "*.nemesis", "*.ocean", "*.rose", "*.[[email protected]].blocking", "*.Node0", "*.supported2017", "RECOVER-FILES.html", "READ_ME_ASAP.txt", "_iWasHere.txt", "!!!SAVE YOUR FILES!.bmp", "!!!!!SAVE YOUR FILES!!!!.txt", "@decrypt_your_files.txt", "HowToDecryptIMPORTANT!.txt", "*.WINDOWS", "*.bbqb", "*.725", "*.DG", "*.Srpx", "*.freefoam", "*.MyChemicalRomance4EVER", "*.extension.srpx", "*.fuck_you_av_we_are_not_globe_fake", "*.BRT92", "*.qwqd", "IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT", "*.TGIF", "*.snake", "*.MOLE03", "*.MOLE04", "*.Petya", "*.HAPP", "*.bam!", "*.Atom", "*.GOTHAM", "*.skunk", "*.symbiom_ransomware_locked", "*.CK", "*[email protected]", "*.yl", "*.ZAYKA", "*.NOOB", "*.crptd", "Instruction for file recovery.txt", "*.[[email protected]]", "*.Reyptson", "*.explorer", "*.au1crypt", "*.s1crypt", "*.alosia", "*.korea", "*.POHU", "*.Ransed", "*.EXTE", "_HELP_INSTRUCTION.TXT", "*.Malki", "*.707", "*.A604AF9070", "*.scorpio", "*id-*_[*@*.*].*", "*.Cry128", "*.Cry36", "*.Cry9", "*.xz", "*.readme_txt", "Ransom.rtf", "*.OXR", "*.acc", "*.MOLE01", "*.3ncrypt3d", "*.AZER", "_INTERESTING_INFORMACION_FOR_DECRYPT.TXT", "*.dcry", "*.MOLE00", "*.LoveYou", "*.z3r0", "*.4x82N", "*.63vc4", "*.BELGIAN_COCOA", "RESTORE-.-FILES.txt", "*.moments2900", "*.0x004867", "*.MMM", "*.rat", "*.aleta", "*.ranrans", "*.lalabitch,", "*.gankLocked", "*.ipygh", "*.via", "dllhost.dat", "FE04.tmp", "027cc450ef5f8c5f653329641ec1fed9*.*", "petwrap.exe", "*.lamo", "File_Encryption_Notice.txt", "*.suppose666", "*.mention9823", "*.breeding123", "*.sux", "*.cfm", "*.Wana Decrypt0r Trojan-Syria Editi0n", "Paxynok.html", "*.pscrypt", "*.a990", "Tempimage.jpg", "*.Tesla", "WannaCry.TXT", "*.kuntzware", "*.nsmf", "*.Facebook", "*.pizdosik", "*.[[email protected]].scarab", "*.sux.AES128", "*.cspider", "*.[[email protected]][email protected]", "*.zbt", "*.MOLE02", "your_key.rsa", "OkuBeni.txt", "*@*.blocking", "*.ogre", "*.tax", "StrutterGear.exe", "ReadMe_Important.txt", "Sifre_Coz_Talimat.html", "*.whycry", "!READ.htm", "!_ИНСТРУКЦИЯ_!.txt", "*.cr020801", "*.cerber6", "*.netn6", "*.rnsmwre", "*.ghost", "*.scarab", "IF_YOU_WANT_TO_GET_ALL_YOUR_FILES_BACK_PLEASE_READ_THIS.TXT", "*.R4bb0l0ck", "*.TraNs", "#HOW_TO_UNRIP#.txt", "*.BeethoveN", "* .tdelf", "*.spectre", "mood-ravishing-hd-wallpaper-142943312215.jpg", "Blooper.exe", "SintaLocker.exe", "SintaRun.py", "*.switch", "*.payforunlock", "HOW TO RECOVER ENCRYPTED FILES.TXT", "README_FOR_DECRYPT.txt", "*.dolphin", "*.dviide", "*.sVn", "*.R3K7M9", "*.BMCODE", "*.zilla", "*.RaaS", "*.resurrection", "*.lost", "*.ram", "*.master", "*.brickr", "READ_DECRYPT_FILES.txt", "*.ramen", "*.TRMT", "*.gommemode", "*.andonio", "*.phantom", "*.r3store", "Read me for help thanks.txt", "*.imsorry", "help_to_decrypt.txt", "*.YYTO", "*.read_to_txt_file.yyto", "*.beep", "*.666", "AArI.jpg", "*.crying", "*.antihacker2017", "*.theworldisyours", "*.spora", "*.sexy", "*[email protected]", "*.pays", "*.payrms", "*.paymts", "*.paymrss", "*.paym", "*.lol", "*.madebyadam", "*.locklock", "*.lcked", "*.kyra", "*.kernel_time", "*.kernel_pid", "*.kernel_complete", "*.ifuckedyou", "*.grt", "*.crypte", "*.cbu1", "*[email protected][email protected]", "*.beef", "*.write_us_on_email", "*.LIGHTNING", "*.xfile", "DECRYPTION.TXT", "*.oled", "*.wtdi", "*.4rwcry4w", "*.Encrypted_By_VMola.com", "*.wlu", "Restore_maysomware_files.html", "*.maysomware", "*.damoclis", "*[email protected]", "*.VisionCrypt", "*.pwned", "how_to_back_files.html", "*.hNcrypt", "*.~xdata~", "*.b0ff", "Galaperidol.exe", "HOW_CAN_I_DECRYPT_MY_FILES.txt", "*.xdata", "Hello There! Fellow @kee User!.txt", "*.kee", "*.grux", "Restore_your_files.txt", "READ_ME.html", "*.mordor", "*.die", "*.SaMsUnG", "!#_DECRYPT_#!.inf", "*.nuke55", "*.onyon", "*.blocked", "!Please Read Me!.txt", "!WannaDecryptor!.exe.lnk", "*.DARKCRY", "*.wincry", "*.wncrypt", "WannaCrypt 4.0.exe", "t.wry", "*.vCrypt1", "*.theva", "*.PAY", "tor.exe", "tasksche.exe", "wcry.zip", "taskhsvc.exe", "taskse.exe", "taskdl.exe", "*.pky", "*.eky", "wcry.exe", "Wannacry.exe", "@WanaDecryptor@.*", "*.slvpawned", "*.WCRYT", "*.WRNY", "*.LOCKED.txt", "*.wncryt", "*.wnry", "*.viki", "RESTORE-12345-FILES.TXT", "*[email protected]", "*.block_file12", "*.@decrypt2017", "*.vdul", "*.2cXpCihgsVxB3", "*.son", "loptr-*.htm", "*.paycyka", "*.medal", "*.bagi", "@[email protected]", "*.wncry", "_!!!_README_!!!_*", "_!!!_README_!!!_*_.hta", "_!!!_README_!!!_*_ .txt", "*.news", "*.corrupted", "HOW_TO_DECRYPT_FILES.html", "*.shifr", "DECRYPT_INFO.txt", "*.FailedAccess", "Cversions.2.db", "*[email protected].*", "ReadME_Decrypt_Help_*.html", "*.fartplz", "* .vCrypt1", "*.xncrypt", "*.Lockify", "*.htrs", "*.cryptowin", "*.owned", "*.x0lzs3c", "*.UIWIX", "*.CRYPTOBOSS", "*.loptr", "*.jaff", "*.bitkangoroo", "*.cloud", "zcrypt.exe", "*[email protected]", "*_luck", "*.decrypt2017", "*.[[email protected]].*.WALLET", "*.[[email protected]].*.WALLET", "*.[[email protected]].*.WALLET", "#_RESTORING_FILES_#.TXT", "*.haters", "*.anon", "*.amnesia", "*.keepcalm", "*.MIKOYAN", "RESTORE_FILES.HTML", "*.WWW", "*.CRYPTED000007", "*[email protected]", "HOW_RETURN_FILES.TXT", "*.MAYA", "*[email protected]", "*.CRYPTOBYTE", "*.AES", "NOTE;!!!-ODZYSKAJ-PLIKI-!!!.TXT", "INSTRUCTION_FOR_HELPING_FILE_RECOVERY.txt", "*.ADR", "*.NM4", "DesktopOsiris.*", "OSIRIS-*.*", "redchip2.exe", "*.LOLI", "ATLAS_FILES.txt", "*.whatthefuck", "*.loveyouisreal", "*.okokokokok", "*.ranranranran", "READ_IT_FOR_GET_YOUR_FILE.txt", "*.psh", "*.GETREKT", "*.one", "!!! READ THIS - IMPORTANT !!!.txt", "*.aes_ni_0day", "*.JEEPERS", "PAYMENT-INSTRUCTIONS.TXT", "*.LOCKOUT", "*.ATLAS", "*[email protected]", "*.AES-NI", "*.DEXTER", "*.CONFICKER", "*.ONION", "*.[[email protected]].WALLET", "*.LCKD", "*.MOLE", "*.RANSOM", "*.lambda.l0cked", "009-READ-FOR-DECCCC-FILESSS.html", "_READ_THI$_FILE_*", "*.I'WANT MONEY", "*.gembok", "!Decrypt-All-Files-*.txt", "*.[[email protected]],CRP", "*.SERP", "*.kilit", "0_HELP_DECRYPT_FILES.HTM", "HUR_DEKRYPTERA_FILER.html", "HUR_DEKRYPTERA_FILER.txt", "*.LAMBDA.LOCKED", "*[email protected]", "*.SKJDTHGHH", "*.LOCK75", "*.B10CKED", "*[email protected]", "*.IWANT", "*.Fuck_You", "Recupere seus arquivos aqui.txt", "READ TO UNLOCK FILES.salsa.*.html", "*.SALSA222", "*.NUMBERDOT", "How Decrypt My Files.lnk", "How_Decrypt_My_Files", "*.CRADLE", "*.ID-7ES642406.CRY", "READ ME ABOUT DECRYPTION.txt", "*.Do_not_change_the_file_name.cryp", "*.pr0tect", "*.android", "*_READ_THIS_FILE_*_*", "*.btcware", "*[email protected]*", "*.AngleWare", "*.zorro", "*.CIFGKSAFFSFYGHD", "*.A9V9AHU4", "*.payfordecrypt", "OKU.TXT", "ZINO_NOTE.TXT", "*.ZINO", "*.kirked", "*.CRPTXXX", "HOW_TO_FIX_!.TXT", "*.[[email protected]].BRAINCRYPT", "*.pizdec", "*.REVENGE ", "!!!READ_TO_UNLOCK!!!.TXT", "*[email protected]", "*.warn_wallet", "*.nemo-hacks.at.sigaint.org", "*.MATRIX", "Crytp0l0cker.Upack.dll", "Crytp0l0cker.dll", "Crytp0l0cker.exe", "decrypted_files.dat", "padcryptUninstaller.exe", "PadCrypt.exe", "Vape Launcher.exe", "READ_ME_!.txt", "*.enjey", "Aescrypt.exe", "*.GG", "*.[[email protected]]", "*[email protected]", "*.CEBER3", "IF_WANT_FILES_BACK_PLS_READ.html", "*.iaufkakfhsaraf", "_HELP_HELP_HELP_*", "zXz.html", "*.zXz", "VictemKey_*_*", "HVORDAN_DU_GENDANNER_FILER.html", "HVORDAN_DU_GENDANNER_FILER.txt", "HELP_ME_PLEASE.txt", "!_RECOVERY_HELP_!.txt", "PLEASE-READIT-IF_YOU-WANT.html", "*.filegofprencrp", "COME_RIPRISTINARE_I_FILE.*", "fattura_*.js", "*[email protected]_", "COMO_ABRIR_ARQUIVOS.txt", "*[email protected][email protected]", "*.kr3", "COMO_RESTAURAR_ARCHIVOS.txt", "COMO_RESTAURAR_ARCHIVOS.html", "*.ENCR", "*.[[email protected]].mails", "[email protected]*", "*.tmp.exe", "What happen to my files.txt", "*[email protected]", "*.BarRax", "*.damage", "*.locked-*", "*.jey", "*.CRYPTOSHIEL", "*.cfk", "ASSISTANCE_IN_RECOVERY.txt", "#_DECRYPT_ASSISTANCE_#.txt", "*.lfk", "_HELP_HELP_HELP_*.hta", "_HELP_HELP_HELP_*.jpg", "BTC_DECRYPT_FILES.txt", "*.TheTrumpLockerp", "*.TheTrumpLockerf", "*.d4nk", "*.x3mpro", "READ-READ-READ.html", "*.weencedufiles", "*.jse", "*.powned", "[KASISKI]*", "INSTRUCCIONES.txt", "@_USE_TO_FIX_*.txt", "*.happydayzz", "*.hasp", "001-READ-FOR-DECRYPT-FILES.html", "DECRYPT_INFORMATION.html", "Rans0m_N0te_Read_ME.txt", "[email protected]*", "*.hnyear", "*[email protected]", "*.wowwhereismyfiles", "*.decryptional", "*.wowreadfordecryp", "*.7zipper", "*.youransom", "*.gui", "*.Harzhuangzi", "*.encryptedyourfiles", "*HERMES", "[[email protected]].wallet", "*.wcry", "*.velikasrbija", "*.razarac", "*.serpent", "*.msj", "*.szesnl", "_DECRYPT_INFO_szesnl.html", "000-IF-YOU-WANT-DEC-FILES.html", "*.evillock", "*.letmetrydecfiles", "*.yourransom", "*.lambda_l0cked", "*.gefickt", "*.HakunaMatata", "*.CRYPTOSHIELD", "*.weareyourfriends", "MERRY_I_LOVE_YOU_BRUCE.hta", "How decrypt files.hta", "[email protected]*", "[email protected]*", "*.potato", "*.otherinformation", "*.vxLock", "*.rdmk", "*.paytounlock", "TRY-READ-ME-TO-DEC.html", "EMAIL_*_recipient.zip", "*.sage", "*[email protected]", "LEER_INMEDIATAMENTE.txt", "*.killedXXX", "*.doomed", "*.sifreli", "*.MERRY", "000-No-PROBLEM-WE-DEC-FILES.html", "*.noproblemwedecfiles", "WE-MUST-DEC-FILES.html", "*.powerfulldecrypt", "*.stn", "*[email protected]", "*.id-3044989498_x3m", "*.x3m", "READ_ME_TO_DECRYPT_YOU_INFORMA.jjj", "*.wuciwug", "*.kencf", "*.file0locked", "file0locked.js", "CryptoRansomware.exe", "*.VBRANSOM", "_HELP_Recover_Files_.html", "*.oops", "*.deria", "*.RMCM1", "*.Locked-by-Mafia", "*.кибер разветвитель", "*-filesencrypted.html", "decrypt_Globe*.exe", "*.hnumkhotep", "DecryptFile.txt", "*.L0CKED", "NFS-e*1025-7152.exe", "firstransomware.exe", "HELP-ME-ENCED-FILES.html", "*.helpmeencedfiles", "*EdgeLocker*.exe ", "*.edgel", "*.XBTL", "*.firecrypt", "YOUR_FILES_ARE_DEAD.hta", "*.MRCR1", "*.PEGS1", "*.RARE1", "*.airacropencrypted!", "*[[email protected]].*", "WHERE-YOUR-FILES.html", "*.Whereisyourfiles", "*[email protected]", "C-email-*-*.odcodc", "*.maktub", "*.hush", "*.bript", "_*_README.hta", "_*_README.jpg", "HOW_OPEN_FILES.hta", "*.gangbang", "GJENOPPRETTING_AV_FILER.html", "GJENOPPRETTING_AV_FILER.txt", "!!! HOW TO DECRYPT FILES !!!.txt", "*.braincrypt", "INSTRUCTION RESTORE FILE.TXT", "*.lesli", "Survey Locker.exe", "!!!!!ATENÇÃO!!!!!.html", "Receipt.exe", "WindowsApplication1.exe", "HWID Lock.exe", "VIP72.exe", "DALE_FILES.TXT", "*.DALE", "*.8637", "*.kok", "HOW_TO_RESTORE_YOUR_DATA.html", "*.paymrts", "*.paymds", "RESTORE_CORUPTED_FILES.HTML", "[email protected]", "Cyber SpLiTTer Vbs.exe", "*.flyper", "000-PLEASE-READ-WE-HELP.html", "*[email protected]", "*.VforVendetta", "popcorn_time.exe", "*.filock", "*.wallet", "*_.rmd", "*.uDz2j8mv", "OSIRIS-*.htm", "DesktopOsiris.htm", "*[[email protected]]*", "*.no_more_ransom", "[email protected]", "*.lovewindows", "*.osiris", "*.R.i.P", "Important!.txt", "!_HOW_TO_RESTORE_*.txt", "HOW_TO_RESTORE_FILES.txt", "_README_*.hta", "*.Zzzz", "*[[email protected]].wallet", "*.coin", "*.crypted_file", "*.EncrypTile", "*.hcked", "_README_.hta", "Runsome.exe", "Payment_Advice.mht", "lblBitcoinInfoMain.txt", "lblFinallyText.txt", "lblMain.txt", "*.hannah", "*.vindows", "How to decrypt your files.jpg", "How to decrypt your files.txt", "How to get data back.txt", "*.zycrypt", "*.sgood", "*.zzzzz", "xort.txt", "DOSYALARINIZA ULAŞMAK İÇİN AÇINIZ.html", "HOWTO_RECOVER_FILES_*.TXT", "HELP_RESTORE_FILES_*.TXT", "Recovery+*.html", "Recovery+*.txt", "_H_e_l_p_RECOVER_INSTRUCTIONS+*.png", "_H_e_l_p_RECOVER_INSTRUCTIONS+*.html", "help_recover_instructions+*.html", "help_recover_instructions+*.BMP", "_how_recover+*.html", "_how_recover+*.txt", "ThxForYurTyme.txt", "_HOW_TO_Decrypt.bmp", "_RECOVER_INSTRUCTIONS.ini", "###-READ-FOR-HELLPP.html", "rtext.txt", "DECRYPTION INSTRUCTIONS.txt", "decrypt explanations.html", "_WHAT_is.html", "_HOWDO_text.html", "readme_liesmich_encryptor_raas.txt", "_Adatok_visszaallitasahoz_utasitasok.txt", "How to", "restore files.hta", "locked.bmp", "README_TO_RECURE_YOUR_FILES.txt", "Your files encrypted by our friends !!!.txt", "ATTENTION.url", "@WARNING_FILES_ARE_ENCRYPTED.*.txt", "README!!!.txt", "# README.hta", "!Recovery_*.html", "YourID.txt", "recover.bmp", "recover.txt", "README HOW TO DECRYPT YOUR FILES.HTML", "READ_IT.txt", "*.lock93", "*.!emc", "*.adk", "svchosd.exe", "*.aesir", "*.CHIP", "*.happy", "*.angelamerkel", "*.razy1337", "*.zendr4", "*.dharma", "*.locked3", "*.duhust", "*.exploit", "*_crypt", "*_help_instruct*.*", "*!DMAlock*", "*.GSupport3", "*.rnsmwr", "*.dCrypt", "ransomed.html", "*.Alcatraz", "*_WHAT_is.html", "readme.hta", "*.96e2", "*.thor", "*.dxxd", "*.usr0", "*.shit", "*.coded", "*.raid10", "*.realfs0ciety*", "*.rip", "*.okean*", "*.globe", "*.nuclear55", "*.1txt", "*.kostya", "*.k0stya", "*.comrade", "*.exotic", "*.fuck", "*.Yakes", "*.Zimbra", "[email protected]*.id-*-*.randomname-*", "*._AiraCropEncrypted!", "README_RECOVER_FILES_*.txt", "README_RECOVER_FILES_*.png", "README_RECOVER_FILES_*.html", "*.~HL*", "[email protected]___*", "*.zc3791", "*.venusp", "*.shino", "*.bleepYourFiles", "*.crashed", "*.amba", "*.7h9r", "*.已加密", "*.암호화됨", "*.b5c6", "*.ap19", "*.a19", "_*_HOWDO_text.html", "*_HOWDO_text.bmp", "*_HOWDO_text.html", "*.odin", "*.zypto*", "zzzzzzzzzzzzzzzzzyyy", "zycrypt.*", "*decrypt your file*.*", "*_nullbyte*", "*.bart", "*.axx", "_H_e_l_p_RECOVER_INSTRUCTIONS+*.txt", "HOW-TO-DECRYPT-FILES.HTML", "HOW_TO_DECRYPT.HTML", "exit.hhr.obleep", "UnblockFiles.vbs", "README_DECRYPT_HYDRA_ID_*.txt", "DECRYPT_Readme.TXT.ReadMe", "Decrypt All Files *.bmp", "HowDecrypt.gif", "HELP_YOURFILES.HTML", "HOW TO DECRYPT FILES.HTML", "BUYUNLOCKCODE", "BitCryptorFileList.txt", "*.crjocker", "*.POSHKODER", "*.hydracrypt_ID_*", "*.CTBL2", "*.unbrecrypt_ID_*", "*.padcrypt", "*.rekt", "*.CCCRRRPPP", "*.SecureCrypte", "*.windows10", "*.pdcr", "*.keybtc@inbox", "*.breaking_bad", "*.cryptowall", "*.xorist", "*.crypt1", "How_to_decrypt_your_files.jpg", "How_to_restore_files.hta", "*.cerber3", "*.a5zfn", "*.purge", "*.fantom", "*.cerber2", "!readme.*", "Como descriptografar seus arquivos.txt", "*.C0rp0r@c@0Xr@", "*.domino", "*cerber2", "*.cawwcca", "how_to_unlock*.*", "!Recovery_*.txt", "Read_this_file.txt", "*.legion", "*.encoderpass", "*.cryptolocker", "*.7z.encrypted", "ATTENTION!!!.txt", "HELP_DECRYPT.lnk", "how to decrypt aes files.lnk", "restore_files.txt", "HowDecrypt.txt", "$RECYCLE.BIN.{*-*-*-*}", "*.heisenberg", "*.breaking bad", "*.razy", "*.Venusf", ".~", "*[email protected]", "winclwp.jpg", "wie_zum_Wiederherstellen_von_Dateien.txt", "tox.html", "strongcrypt.bmp", "qwer2.html", "qwer.html", "pronk.txt", "paycrypt.bmp", "maxcrypt.bmp", "how_decrypt.gif", "how to get data.txt", "help_recover_instructions*.txt", "help_recover_instructions*.html", "help_recover_instructions*.bmp", "help-file-decrypt.enc", "enigma_encr.txt", "enigma.hta", "default432643264.jpg", "default32643264.bmp", "decypt_your_files.html", "de_crypt_readme.txt", "de_crypt_readme.html", "de_crypt_readme.bmp", "cryptinfo.txt", "crjoker.html", "_how_recover*.txt", "_how_recover*.html", "_Locky_recover_instructions.bmp", "_H_e_l_p_RECOVER_INSTRUCTIONS*.txt", "_H_e_l_p_RECOVER_INSTRUCTIONS*.png", "_H_e_l_p_RECOVER_INSTRUCTIONS*.html", "_HELP_instructions.txt", "_HELP_instructions.bmp", "_DECRYPT_INFO_*.html", "Your files encrypted by our friends !!! txt", "Your files are locked !.txt", "Your files are locked !!.txt", "Your files are locked !!!.txt", "Your files are locked !!!!.txt", "YOUR_FILES_ARE_LOCKED.txt", "YOUR_FILES_ARE_ENCRYPTED.TXT", "YOUR_FILES_ARE_ENCRYPTED.HTML", "YOUGOTHACKED.TXT", "UNLOCK_FILES_INSTRUCTIONS.txt", "UNLOCK_FILES_INSTRUCTIONS.html", "SIFRE_COZME_TALIMATI.html", "SHTODELATVAM.txt", "Read Me (How Decrypt) !!!!.txt", "RESTORE_FILES_*.txt", "RESTORE_FILES_*.*", "READ_THIS_TO_DECRYPT.html", "README_HOW_TO_UNLOCK.TXT", "README_HOW_TO_UNLOCK.HTML", "README_DECRYPT_UMBRE_ID_*.txt", "README_DECRYPT_UMBRE_ID_*.jpg", "README_DECRYPT_HYRDA_ID_*.txt", "READ ME FOR DECRYPT.txt", "READ IF YOU WANT YOUR FILES BACK.html", "Payment_Instructions.jpg", "ONTSLEUTELINGS_INSTRUCTIES.html", "OKSOWATHAPPENDTOYOURFILES.TXT", "MENSAGEM.txt", "KryptoLocker_README.txt", "Instructionaga.txt", "ISTRUZIONI_DECRITTAZIONE.html", "INSTRUCTIONS_DE_DECRYPTAGE.html", "INSTRUCCIONES_DESCIFRADO.html", "INSTALL_TOR.URL", "IMPORTANT.README", "IMPORTANT READ ME.txt", "Howto_RESTORE_FILES.html", "How to decrypt your data.txt", "How to decrypt LeChiffre files.html", "Help Decrypt.html", "Hacked_Read_me_to_decrypt_files.html", "HOW_TO_UNLOCK_FILES_README_*.txt", "HOW_TO_RESTORE_FILES.html", "HOW_DECRYPT.URL", "HOW_DECRYPT.TXT", "HOW_DECRYPT.HTML", "HOWTO_RECOVER_FILES_*.*", "HOW TO DECRYPT FILES.txt", "HELP_YOUR_FILES.html", "HELP_YOUR_FILES.PNG", "HELP_TO_SAVE_FILES.bmp", "HELP_RESTORE_FILES_*.*", "HELP_DECRYPT.URL", "HELP_DECRYPT.PNG", "HELP_DECRYPT.HTML", "GetYouFiles.txt", "File Decrypt Help.html", "FILES_BACK.txt", "ENTSCHLUSSELN_HINWEISE.html", "DecryptAllFiles*.txt", "DESIFROVANI_POKYNY.html", "DECRYPT_YOUR_FILES.txt", "DECRYPT_YOUR_FILES.HTML", "DECRYPT_ReadMe1.TXT", "DECRYPT_INSTRUCTIONS.html", "DECRYPT_INSTRUCTION.URL", "DECRYPT_INSTRUCTION.HTML", "DECRYPTION_HOWTO.Notepad", "Comment débloquer mes fichiers.txt", "BUYUNLOCKCODE.txt", "AllFilesAreLocked*.bmp", "4-14-2016-INFECTION.TXT", "*_ryp", "*_HELP_instructions.html", "*.xcrypt", "*.unavailable", "*.szf", "*.porno.pornoransom", "*.plauge17", "*.neitrino", "*.kimcilware.locked", "*.iwanthelpuuu", "*.herbst", "*[email protected]", "*.h3ll", "*.gws.porno", "*.fuckyourdata", "*.encrypted.locked", "*.cryptz", "*.crypttt", "*.cripttt", "*.criptokod", "*.criptiko", "*.btc.kkk.fun.gws", "*.aga", "*._ryp", "*.Where_my_files.txt", "*.Read_Me.Txt", "*.RSplited", "*.KEYZ.KEYH0LES", "*.How_To_Get_Back.txt", "*.How_To_Decrypt.txt", "*.Contact_Here_To_Recover_Your_Files.txt", "*.31392E30362E32303136_*", "# DECRYPT MY FILES #.vbs", "#", "DECRYPT MY FILES #.txt", "# DECRYPT MY FILES #.html", "!Where_are_my_files!.html", "!!!README!!!*.rtf", "!!!-WARNING-!!!.txt", "!!!-WARNING-!!!.html", "*.magic_software_syndicate", "*[email protected]", "*.crypt", "*.bitstak", "*.wflx", "*.CRRRT", "howtodecryptaesfiles.txt", "!satana!.txt", "*.akaibvn", "*.cRh8", "*.YTBL", "*.krypted", "*.tzu", "*.6FKR8d", "*.sshxkej", "*.eclr", "*.epic", "*.paybtcs", "*.AFD", "*.paymst", "*.payms", "*.isis", "*.zepto", "*.bart.zip", "*.kratos", "*.31342E30362E32303136*", "*.SecureCrypted", "*.crptrgr", "*.rtyrtyrty", "!DMALOCK3.0*", "*.evil", "*.crypt38", "*.asdasdasd", "*.ded", "*.bloccato", "*.canihelpyou", "*.crypz", "decrypt-instruct*.*", "*files_are_encrypted.*", "*decryptmyfiles*.*", "help_instructions.*", "*-recover-*.*", "de_crypt_readme.*", "*!recover!*.*", "*recover}-*.*", "*rec0ver*.*", "_help_instruct*.*", "*_recover_*.*", "*+recover+*.*", "*warning-!!*.*", "*decrypt my file*.*", "help_file_*.*", "recovery+*.*", "readme_for_decrypt*.*", "install_tor*.*", "readme_decrypt*.*", "howtodecrypt*.*", "howto_restore*.*", "how_to_recover*.*", "how_recover*.*", "how_to_decrypt*.*", "how to decrypt*.*", "help_restore*.*", "help_your_file*.*", "help_recover*.*", "help_decrypt*.*", "decrypt_instruct*.*", "cryptolocker.*", "*recover_instruction*.*", "*.hydracrypt_ID*", "*gmail*.crypt", "*.cryptotorlocker*", "*.xxx", "*.xyz", "*.xtbl", "*.xort", "*.xrtn", "*.vvv", "*.vscrypt", "*.trun", "*.ttt", "*.surprise", "*.troyancoder@qq_com", "*.sport", "*.scl", "*.ryp", "*.sanction", "*.RRK", "*.rokku", "*.remind", "*.relock@qq_com", "*.RDM", "*.RADAMANT", "*.R5A", "*.R4A", "*.PoAr2w", "*.pizda@qq_com", "*.p5tkjw", "*.oplata@qq_com", "*.oshit", "*.oor", "*.one-we_can-help_you", "*.OMG!", "*.nochance", "*.nalog@qq_com", "*.micro", "*.LOL!", "*.locky", "*.locked", "*.LeChiffre", "*.kraken", "*.korrektor", "*.kkk", "*.kimcilware", "*.KEYZ", "*.keybtc@inbox_com", "*.KEYHOLES", "*.justbtcwillhelpyou", "*.infected", "*.helpdecrypt@ukr_net", "*.hb15", "*.ha3", "*.gruzin@qq_com", "*.gws", "*.fun", "*.fucked", "*.enigma", "*.encryptedped", "*.encryptedRSA", "*.encryptedAES", "*.Encrypted", "*.encrypt", "*.encedRSA", "*.EnCiPhErEd", "*.dyatel@qq_com", "*.czvxce", "*.darkness", "*.ctbl", "*.CrySiS", "*.CryptoTorLocker2015!", "*.crypted", "*.cry", "*.crjoker", "*.crinf", "*.crime", "*.coverton", "*.code", "*.clf", "*.chifrator@qq_com", "*.cerber", "*.cbf", "*.btcbtcbtc", "*.btc-help-you", "*.btc", "*.bloc", "*.better_call_saul", "*.AES256", "*.{CRYPTENDBLACKDC}", "*.73i87A", "*.zzz", "*.abc", "*.aaa", "vault.txt", "vault.key", "recovery_key.txt", "vault.hta", "message.txt", "recovery_file.txt", "confirmation.key", "enc_files.txt", "last_chance.txt", "*.vault", "*want your files back.*", "*.frtrss", "*.exx", "*.ezz", "*.ecc", "*help_restore*.*", "*how_to_recover*.*", "*restore_fi*.*", "*ukr.net*", "*qq_com*", "*keemail.me*", "*decipher*", "*install_tor*.*", "*@india.com*", "*@gmail_com_*", "*.*obleep", "*.*exx", "*.*locked", "*.*nochance", "*.*kraken", "*.*kb15", "*.*darkness", "*.*crypto", "*.*cry", "_Locky_recover_instructions.txt", "help_recover_instructions+*.txt", "recoverfile*.txt", "Howto_Restore_FILES.TXT", "recoveryfile*.txt", "_how_recover.txt", "howrecover+*.txt", "restorefiles.txt", "howto_recover_file.txt", "HowtoRESTORE_FILES.txt", "RECOVERY_FILE*.txt", "RECOVERY_FILES.txt", "help_decrypt_your_files.html", "HELPDECYPRT_YOUR_FILES.HTML", "IHAVEYOURSECRET.KEY", "SECRET.KEY", "SECRETIDHERE.KEY", "READTHISNOW!!!.TXT", "IAMREADYTOPAY.TXT", "HELLOTHERE.TXT", "FILESAREGONE.TXT", "DECRYPT_ReadMe.TXT", "Read.txt", "About_Files.txt", "_secret_code.txt", "ReadDecryptFilesHere.txt", "Coin.Locker.txt", "HOW_TO_DECRYPT_FILES.TXT", "DECRYPT_INSTRUCTION.TXT", "encryptor_raas_readme_liesmich.txt", "Help_Decrypt.txt", "YOUR_FILES.url", "How_To_Recover_Files.txt", "YOUR_FILES.HTML", "INSTRUCCIONES_DESCIFRADO.TXT", "DECRYPT_INSTRUCTIONS.TXT", "HELP_TO_SAVE_FILES.txt", "DecryptAllFiles.txt", "HELP_RECOVER_FILES.txt", "HELP_RESTORE_FILES.txt", "HELP_TO_DECRYPT_YOUR_FILES.txt", "HELP_YOUR_FILES.TXT", "HELPDECRYPT.TXT", "*.CTB2", "*.SUPERCRYPT", "*.magic", "*.1999", "*.toxcrypt", "*.bleep", "*.0x0", "*.good", "*.R16M01D05", "*.pzdc", "*.XRNT", "*.crypto", "*.ccc", "*.da_vinci_code", "*.payransom", "*.KEYH0LES", "oor.*", "*.zyklon", "*.zcrypt", "*.Z81928819", "*.Silent", "*.RSNSlocked", "*.RAD", "*.porno", "*.pornoransom", "*.odcodc", "_ryp", "*.helpdecrypt@ukr*.net", "*.only-we_can-help_you", "*.cryp1", "*.fileiscryptedhard", "*.blocatto", "*.8lock8", "*.777") |
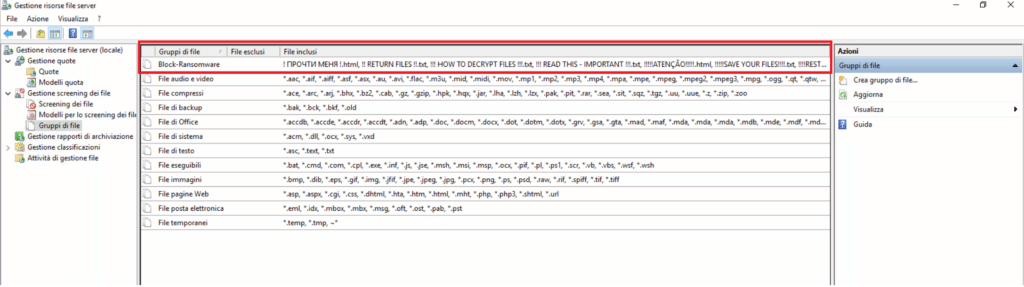
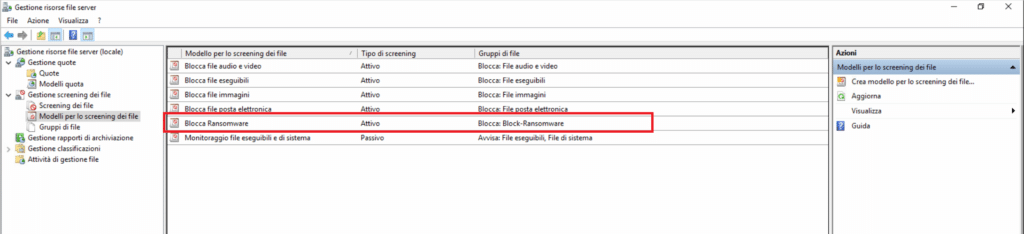
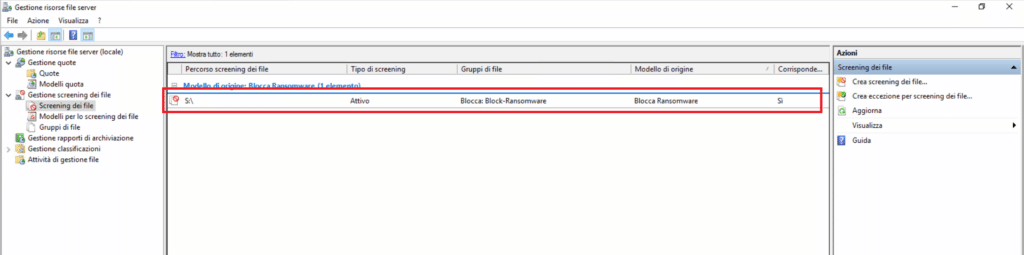
Se andiamo di nuovo sullo snap-in del FSRM noteremo che in corrispondenza del Gruppo Block-Ransomware sono comparse tutte le estensioni che abbiamo caricato via script.
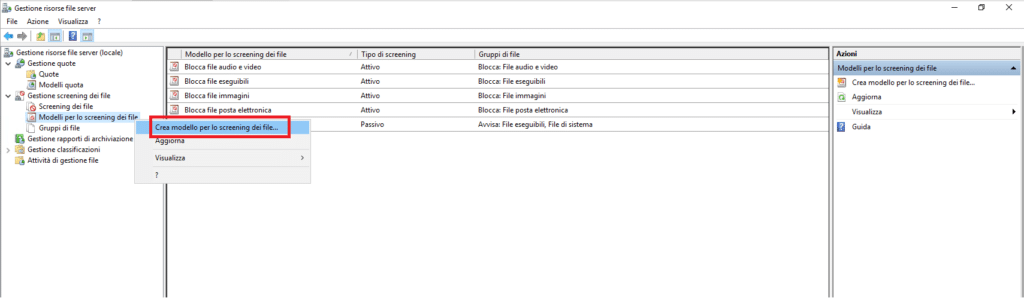
Selezionare sempre dallo snap-in la voce Modelli per lo screening dei file
Cliccare con il tasto destro quindi selzionare Crea modello per lo screening dei file…
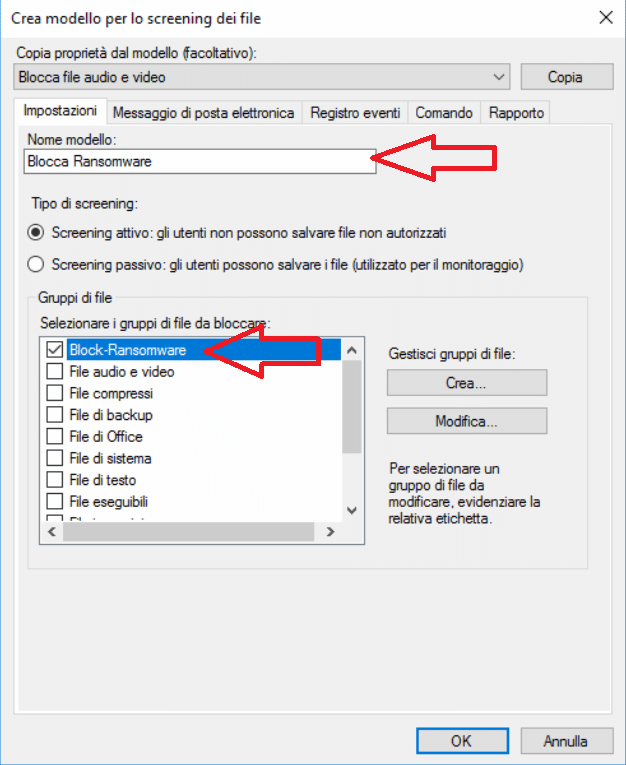
Diamo quindi un nome al modello (Es: Blocca Ransomware) e selezioniamo il gruppo di file da bloccare che abbimo creato in precedenza (Es: Block-Ransomware)
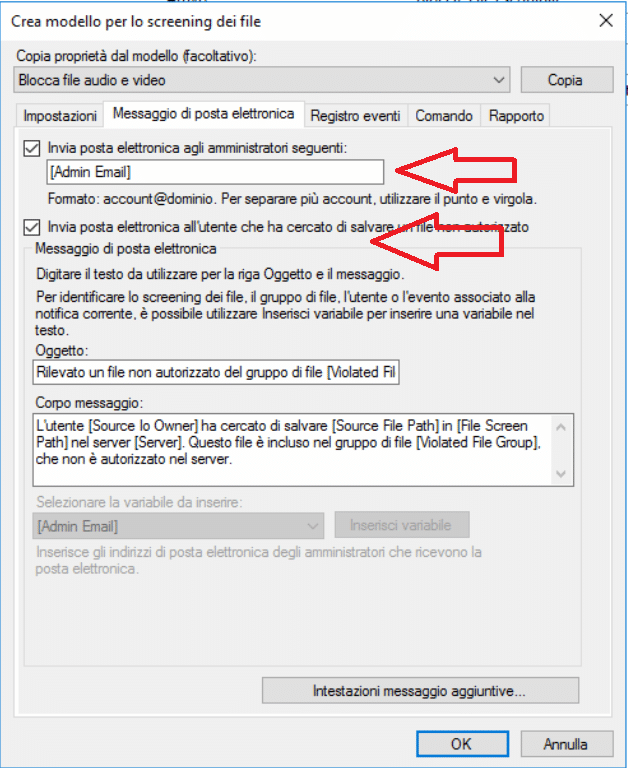
Selezionare il Tab Messaggio di Posta Elettronica e spuntare entrambe le opzioni per inviare una mail all’amministratore e a chi ha cercato di salvare il file in modo da essere sempre allertati in caso di file con estensioni pericolose.
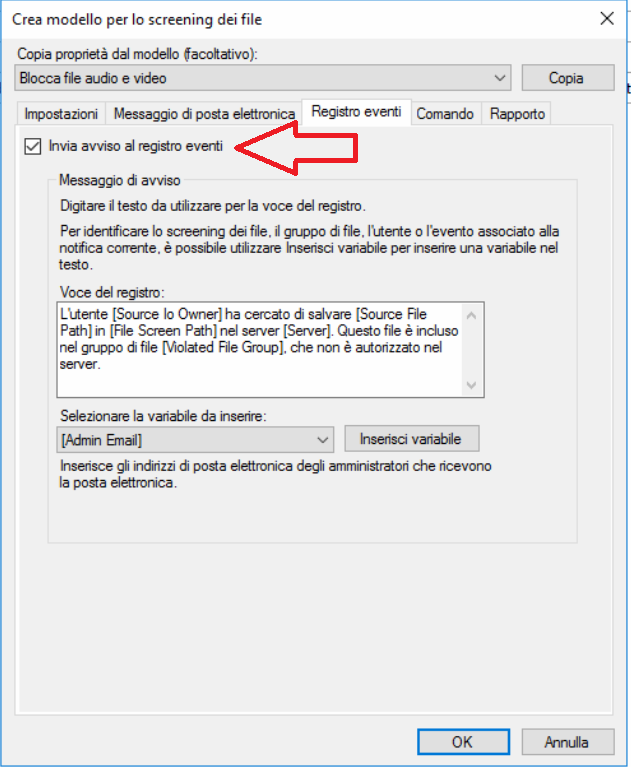
Selezionare il Tab Registro Eventi e spuntare l’opzione Invia avviso al registro eventi se vogliamo registrare all’interno dell’Event Viewer di Microsoft tutti i tentativi di copia di file con estensioni pericolose
Cliccare su OK per confermare tutte le modifiche.
Dovremmo vedere il modello come mostrato nell’immagine sovrastante
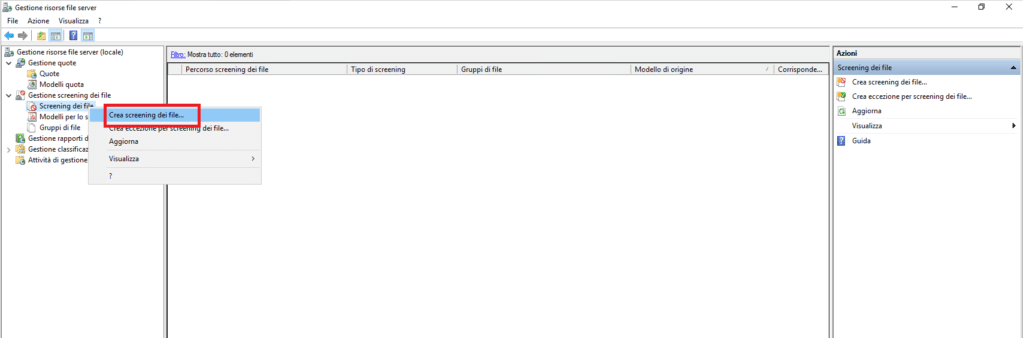
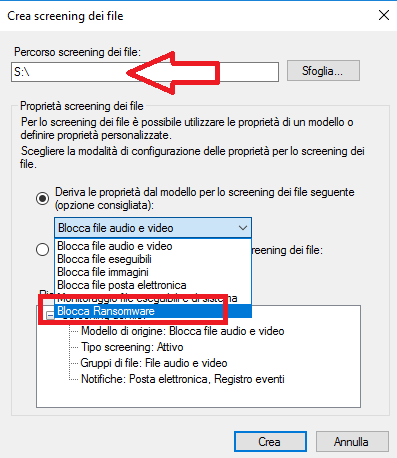
Procedere alla creazione dello screening cliccando con il tasto destro su Screening dei File e selezionando l’opzione Crea screening dei file…
Indicare il path dove si intende applicare lo screening quindi selezionare dal menù a tendina il modello creato in precendenza (Es: Blocca Ransomware)
Cliccare su Crea
Se è tutto corretto dovremmo vedere una schermata come quella sovrastante
Quindi da questo momento in poi ogni qual volta verrà salvato un file con le estensioni vietate verrà bloccata la copia con il classico popup di Windows e verrà inviata una mail all’Amministratore di sistema e una mail all’utente che ha cercato di copiare il file.
Naturalmente la lista delle estensioni pericolose va aggiornata regolarmente.
Ad oggi, alla stesura del tutorial, la lista che ho inserito nello script contiene circa 2400 estensioni pericolose.


















![Errore in LibreNMS: Python3 module issue found: ‘Required packages: [‘PyMySQL!=1.0.0’, ‘python-dotenv’, ‘redis>=4.0’, ‘setuptools’, ‘psutil>=5.6.0’, ‘command_runner>=1.3.0’]](https://www.raffaelechiatto.com/wp-content/uploads/2024/09/Errore_in_LibreNMS_Python3_module_issue_found-1080x675.png)













Buongiorno,
volevo segnalare un problema riscontrato nella mia azienda bloccando la lista di file suggerita da questo articolo:
nella lista compare anche “*.FFF” e questo blocca anche il file “Dummy_test_filedjsjfkdskk.fff” creato dal software ArubeSign durante la firma digitale di qualunque documento impedendo di portare a termine la firma, per cui ho rimosso l’estensione “*.FFF” dalla lista dei possibili ransomware.
Salve il ruolo di screening con FSRM utilizza poca RAM e CPU con accessi normali al file server.
Per esperienza su file server con migliaia di accessi contemporanei utilizza neanche l’1% di RAM e CPU.
Poi dipende anche da quanti files vengono segnalati come dannosi, è chiaro che se contemporaneamente 100 utenti salvano dei file rischiosi il livello di CPU e RAM aumenterà leggermente (ma neanche tanto) rispetto a 10 salvataggi contemporanei.
Però in buona sostanza è un tool davvero valido che consiglio di installare sempre su file server.
Per quanto riguarda la lista delle estensioni basta cercare su internet una volta al mese e di sicuro qualche sito ti tirerà fuori le nuove estensioni di Ransomware.
Io di solito vado sempre su questo sito https://fsrm.experiant.ca/
Qui puoi anche segnalare tu eventuali estensioni dannose.
Ciao e buona giornata
Salve ho letto con interesse diversi articoli sul tuo blog ,che ritengo molto interessante ed esaustivo,e mi chiedevo in particolare riguardo questo tuo post:
1) Sai per caso darmi qualche info sull’impatto ( cpu … ram ) che questo ruolo ha sulle risorse del server ? ( tieni conto che lo installerei esclusivavente per l’azione di filtraggio da te illustrata )
2) da dove si possono prendere le estensioni per aggiornare la lista che hai già costruito ?